Send With Confidence
Partner with the email service trusted by developers and marketers for time-savings, scalability, and delivery expertise.


Time to read: 6 minutes
Brand Indicators for Message Identification (BIMI) is an email authentication standard that companies are adopting to build trust with their email recipients. BIMI adds a verified brand logo next to the email in the recipient’s inbox, which increases deliverability, visibility and trust, and increases your brand recognition.
BIMI works by integrating Domain-based Message Authentication, Reporting and Conformance (DMARC), which is a protocol to verify an email’s integrity and authenticity. After verifying an email, email clients that support BIMI will fetch the associated DNS record for the sender’s domain, which contains a digital certificate with the brand logo embedded.
In this post, we’ll walk through the steps to implement BIMI for your organization’s email program with SendGrid. But first, let’s discuss why you should look at BIMI for your organization.
BIMI is an excellent opportunity for your organization to increase customer trust in another communications channel, increasing brand recognition and making your email communications instantly recognizable.
Here’s what Google has written about BIMI inside Gmail in Google Workspace. And you’ve probably seen other organizations who have adopted BIMI in your own email inbox:


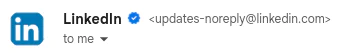

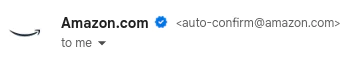

SendGrid has been a leader in helping our customers adapt and comply with the changes to DMARC across the industry, led by Yahoo! and Google. And today, emails sent through SendGrid can be properly aligned with BIMI. Once configured, you’ll be able to immediately take advantage of this feature.
As best practices and standards for trusted communications in email evolve, BIMI allows you an opportunity to build upon your implementation of DMARC, further strengthening your position as a trusted sender and adding the new ability to provide trusted branding to your email communications.
Before getting started, you’ll need an account with SendGrid if you don’t already have one. You can sign up for free here.
We’ll walk through the steps to authenticate your domain and implement BIMI together.
To get started, we’ll describe our initial setup. You should be able to get your environment to a similar state without any issues, preparing you to follow the remaining steps for BIMI implementation.
In our demo, we are owners of a domain, codingplus.coffee. We’ll set up our SendGrid account so that we can send emails from this domain via the SendGrid SMTP server.
For BIMI to work, your brand logo must be publicly accessible and served from the same domain from which you’re sending emails. So, we have a web server running that is serving up our logo at https://www.codingplus.coffee/coding-plus-coffee-logo.svg. We’ll cover details about the file format and other specifications when we get to Step 3 below.
With those initial pieces in place, it’s time to move on to our first step.
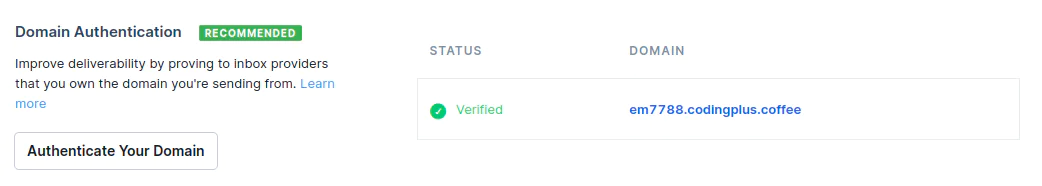
To send emails from SendGrid’s platform, we’ll set up domain authentication to improve deliverability from the codingplus.coffee domain. Then, we’ll set up single sender verification to verify that we own the email address from which we’ll be sending.
First, we sign into SendGrid. Then, we navigate to Settings > Sender Authentication.

Click Authenticate Your Domain.

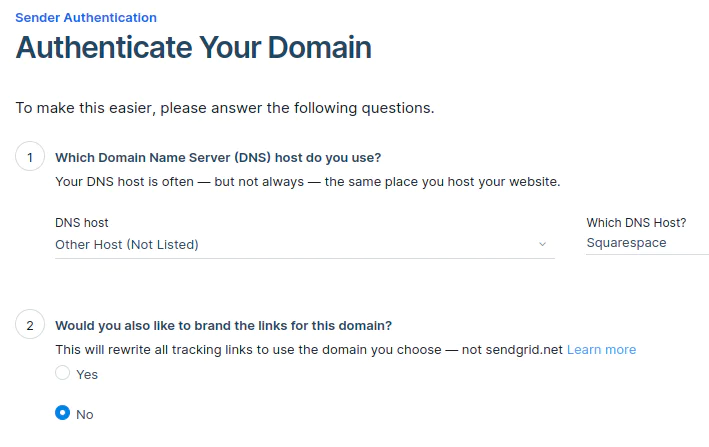
In the first step, select your DNS host, or specify it if it’s not in the list. Then, click Next.

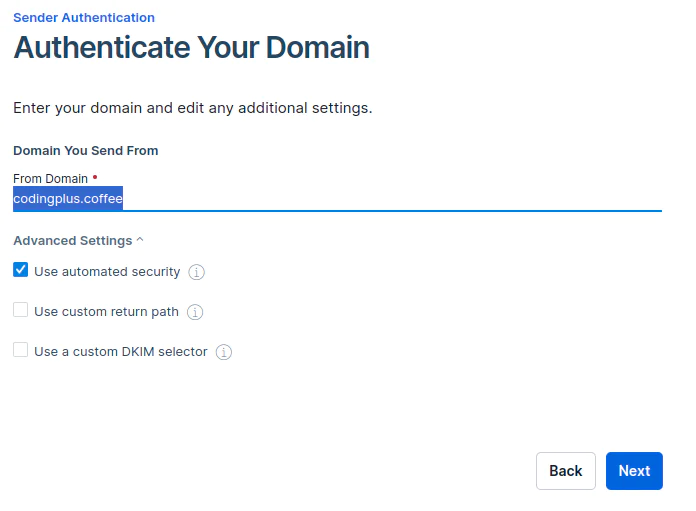
Provide the domain from which you will be sending emails. For our demo, it is codingplus.coffee. Then, click Next.

You’ll then see several DNS records (3 CNAME and 1 TXT) to add for your domain.
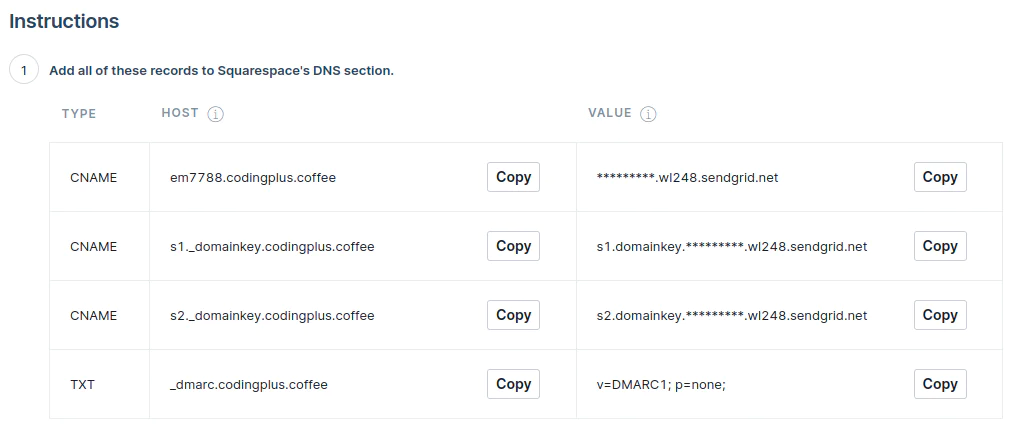

The first CNAME record in the list associates your domain with your SendGrid account, and SendGrid uses it to help with routing click and open tracking to your account.
The CNAME records with _domainkey in the HOST are DomainKeys Identified Mail (DKIM) records, used to confirm the authentication of the sender by verifying and signing emails.
The final TXT record has to do with DMARC, which we’ll discuss in more detail in Step 2.
In addition to these four records, we also want to add a TXT record for sender policy framework (SPF), specifying SendGrid mail servers as the permitted sender. The TXT record should look like this:
Host | Data |
@ | v=spf1 include:sendgrid.net -all |
Navigate to the DNS settings for your domain provider. Add the four records provided by SendGrid, along with this fifth record for SPF.
Note: For some providers, when adding a CNAME or TXT record, you should leave off the domain name that is at the end of the HOST value. For example, if you need a CNAME record with HOST em7788.codingplus.coffee, you might simply provide em7788 as the HOST. Likewise, the HOST for our TXT record would simply be _dmarc (instead of the full _dmarc.codingplus.coffee).
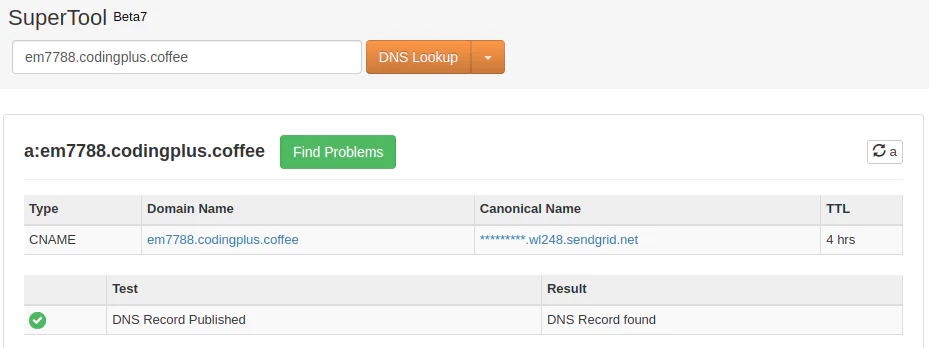
You can use the MX Toolbox to verify that these CNAME and TXT records have been set up correctly. Here’s an example of how we use the tool to verify that CNAME record is in place:

Check the box in SendGrid saying you’ve added these records. Click Verify.
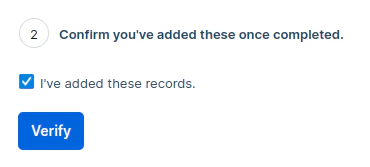

Assuming your DNS records were properly updated, SendGrid will complete authentication of your domain.
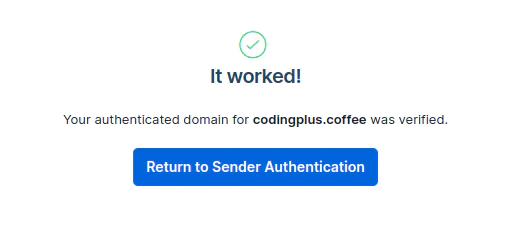

You can read this page for more detailed information on domain authentication with SendGrid.
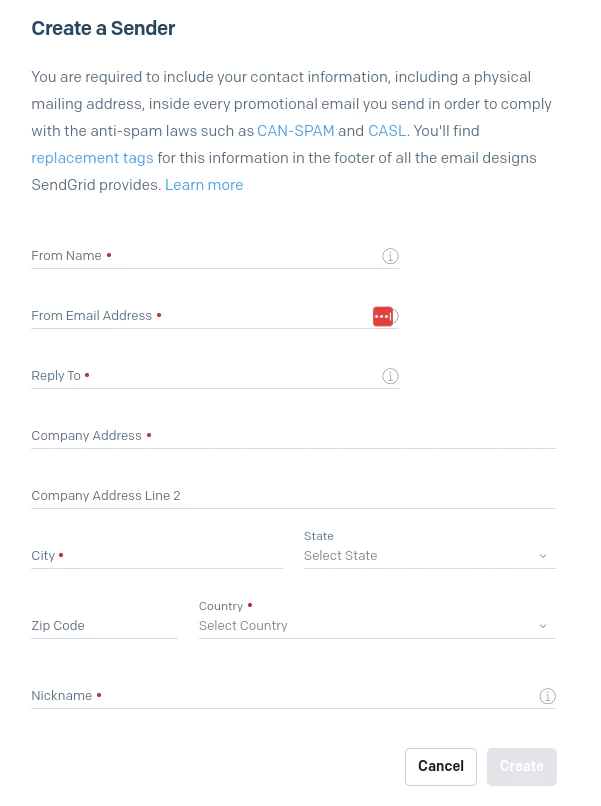
Next, we want to verify that we own the email address from which we’ll be sending our emails. Back on the Sender Authentication page, click Verify a Single Sender.

You’ll see a form with contact information for the email address that you are verifying. Complete this form and click Create.

After completing this step, SendGrid will run its verification process and then add the email address to the list of verified senders.

You’ll recall that we added a DMARC-related record in the previous step. Our TXT record looked like this:
Host | Data |
_dmarc.codingplus.coffee | v=DMARC1; p=none; |

We used basic DMARC settings for that step, because we were only concerned with domain authentication. However, BIMI requires stricter DMARC settings than this. BIMI requires both SPF to be set and DMARC configured to a policy of p=quarantine or p=reject., which signals that you carefully consider the policies and types of email you send from your domain. Also, the percent option (pct) must be set to 100.
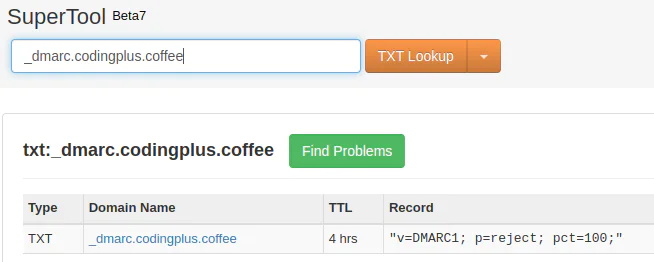
So, we will update our record to use the following value instead:
v=DMARC1; p=reject; pct=100;
A quick check in the MX Toolbox shows our record has been updated successfully.

Note: For more information on DMARC, read this page.
As mentioned earlier, we already created and uploaded our BIMI brand logo file. However, in this section, we’ll walk through the details you need to know for handling this file.
First of all, your BIMI image must follow these guidelines:
We created our brand logo, and it looks like this:


We have an SVG file for our logo that we have hosted in our domain, available at:
https://www.codingplus.coffee/coding-plus-coffee-logo.svg
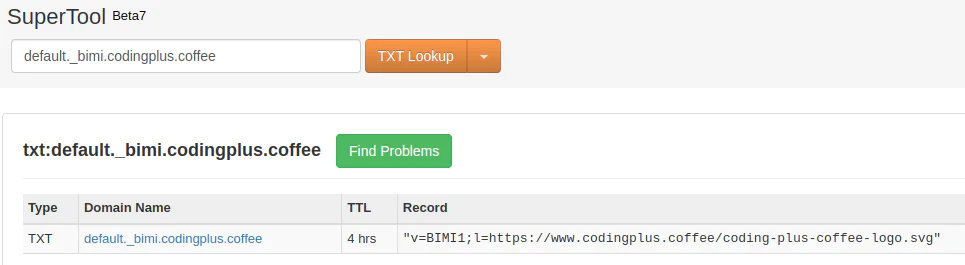
Now, we need to add another TXT record to our domain. The record takes the following form:
Host | Data |
default._bimi.codingplus.coffee | v=BIMI1;l=https://www.codingplus.coffee/coding-plus-coffee-logo.svg |
Warning: The parts above are unique to our domain and SVG file location. Your record will differ here.
This record tells email clients where they can locate the BIMI image to display alongside emails from that domain. For more details on BIMI implementation, check out this page.
After adding our TXT record, we verify it at MX Toolbox.

MX Toolbox also has a BIMI lookup tool, which does more than just analyze the TXT record. When we enter our domain in the tool, here is what we see:
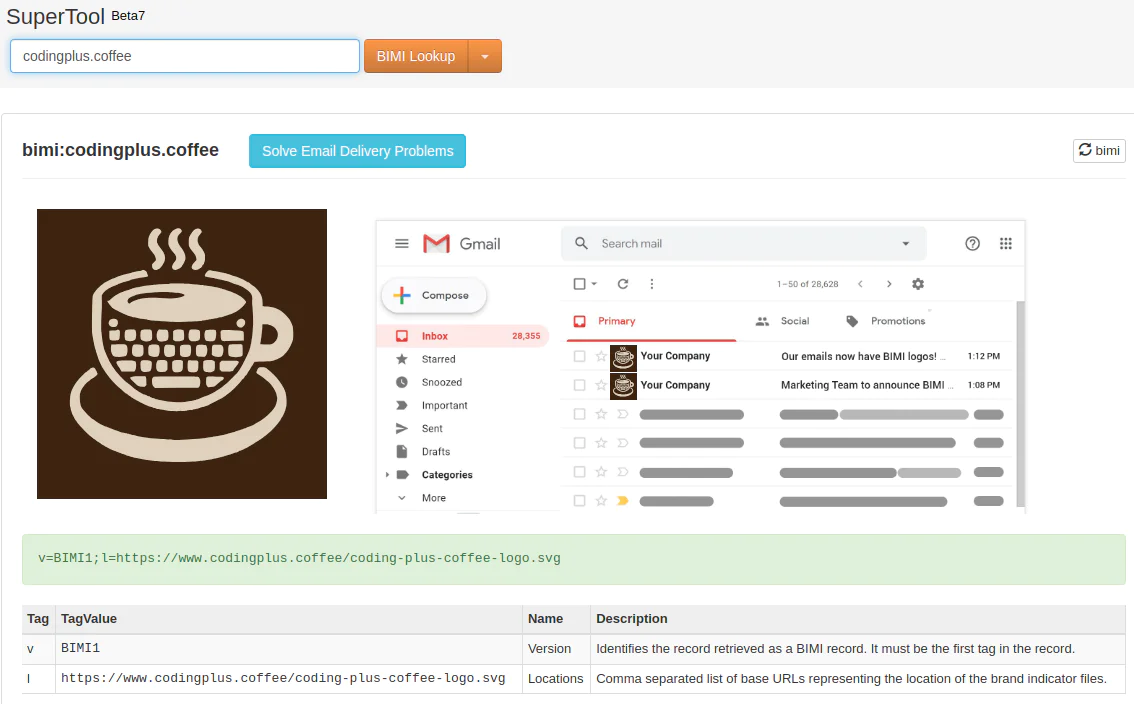

Our BIMI logo is up and running!
This step is optional, but highly recommended. A VMC validates authenticity and ownership of an organization’s logo. An authority verifies your logo and then issues you a PEM file with the SVG logo file embedded in it. Gmail, Yahoo, Apple and many other email clients will only support BIMI through the presence of this PEM file (not through the standalone SVG from Step 3)
If you pursue this, you can obtain a VMC through one of two currently accepted authorities:
Once you obtain a VMC, store the PEM file and serve it on your domain, just like you do your BIMI logo file. Then, you update your TXT record with BIMI information, adding the location of your PEM file.
For example, let’s say we had a VMC file called vmc.pem, served up at https://www.codingplus.coffee/vmc.pem. Then, our TXT record would be updated to look like this:
Host | Data |
default._bimi.codingplus.coffee | v=BIMI1;l=https://www.codingplus.coffee/coding-plus-coffee-logo.svg;a=https://www.codingplus.coffee/vmc.pem |
Again, this step is optional, but you’ll need to obtain a VMC for BIMI to work across all inboxes.
We’ve completed our BIMI implementation. Now, when we send an email from our domain, supported email clients will fetch and insert the verified BIMI logo alongside emails in a recipient’s inbox. This is what the email looks like in Gmail:
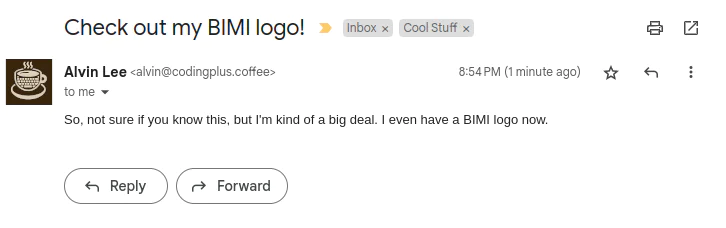

More and more brands are adopting BIMI for their email campaign strategies in order to increase visibility, trust, and brand awareness among current and prospective customers. When your customers see an email purportedly from your domain, seeing the verified and authenticated BIMI brand logo alongside the email will give them more confidence that it’s actually from your company.
In this post, we’ve walked through the steps for implementing BIMI for your domain. It’s simple and straightforward, and it can go a long way toward building brand awareness, email visibility, and recipient trust.
For additional information on using BIMI with SendGrid, you can read more here. Additionally, see our Everything DMARC guide for our overview and best practices.
Are you ready to start using SendGrid to level up your organization’s outgoing email game? Sign up to start using SendGrid for free today.
Partner with the email service trusted by developers and marketers for time-savings, scalability, and delivery expertise.