GitHub and other cloud-based source control systems are awesome, and they’re extremely popular with our customers. The ease with which you can collaborate with developers across the cube or around the world is unparalleled. However, as public source control platforms like GitHub have risen to prominence, suspicious senders have taken note.
When developers accidentally publish their secret keys to GitHub, bad actors are quick to pounce. They have automated the process of discovering AWS secret keys in public GitHub repositories and using these keys to
spin up EC2 instances to mine Bitcoin.
Suspicious senders are also scouring GitHub looking for credentials for ESPs like SendGrid and our competitors. When they find them, they are quick to use these secrets to try to blast spam or phishing messages through our systems.
How to Protect Yourself (or Your Account)
As a SendGrid customer, there are a couple of things you can do to minimize the chances that your account will get taken over by the bad guys. First, make sure you’re using
API keys. These are used by your integrations to authenticate to your SendGrid account instead of sending your username and password. Make sure that the API key you generate for sending mail has permission to send mail, but nothing else.
Next, make sure that your program uses environment variables to store the API key, rather than hardcoding the key into your code. A convention that works well for this is to store the key in a file, outside of your webserver’s document root, and source it before calling your SendGrid integration or at boot time.
Let’s look at an example of using an API key stored in an environment variables with the SendGrid Go library.
First, log into your SendGrid account, and click on “Settings -> API Keys.”
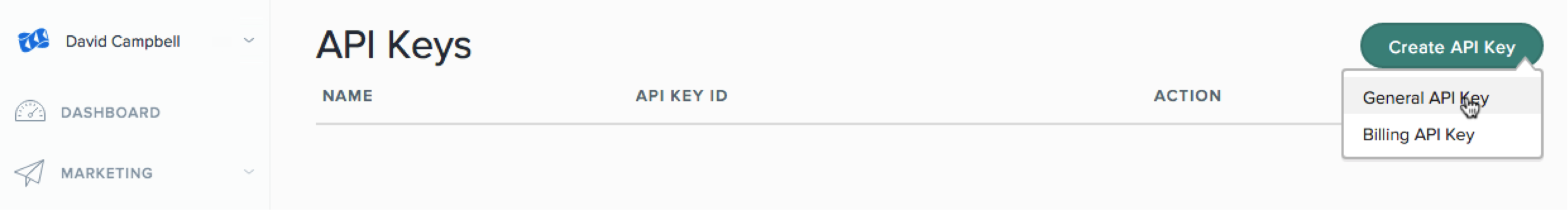
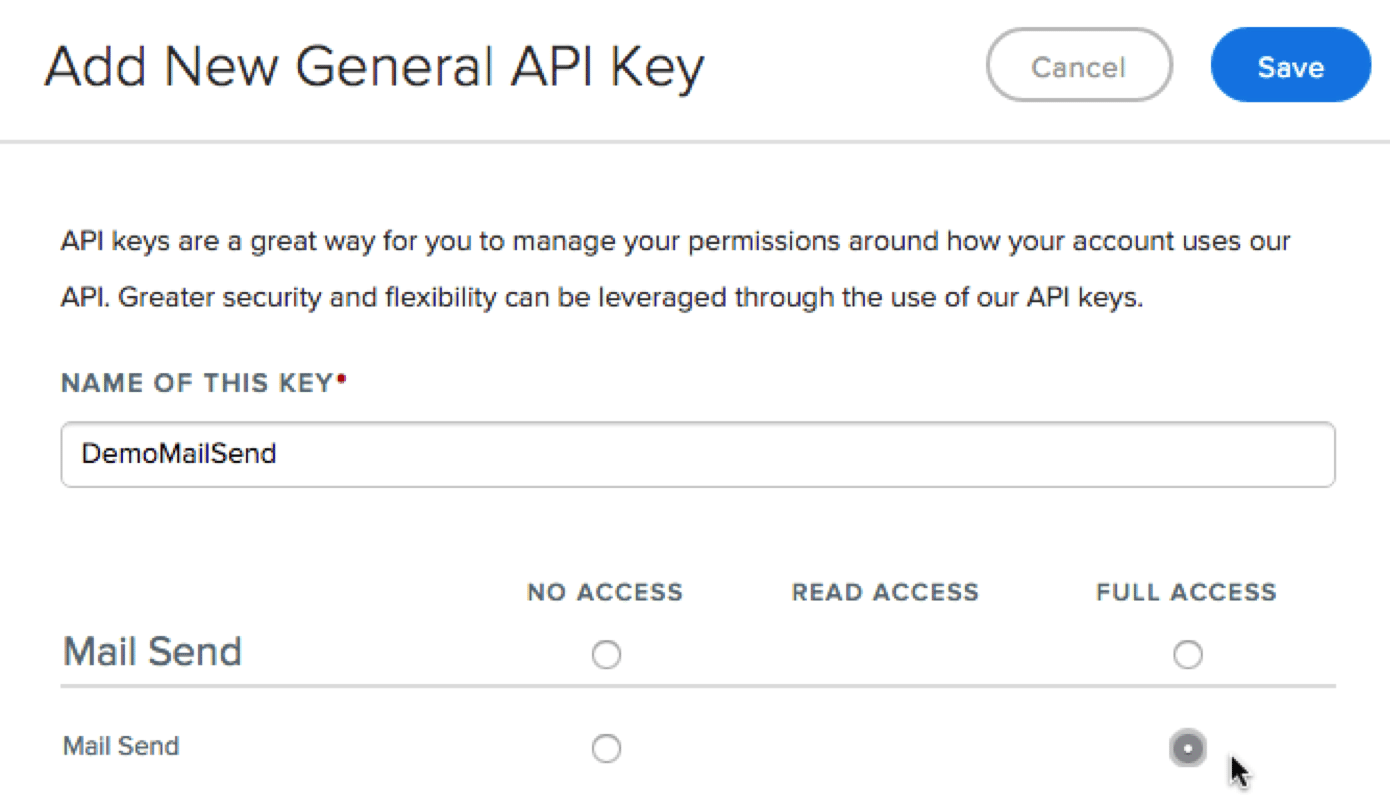
Click “Create API Key,” and then “General API Key." Give the key a name, and only give it “Full Access” to send mail.
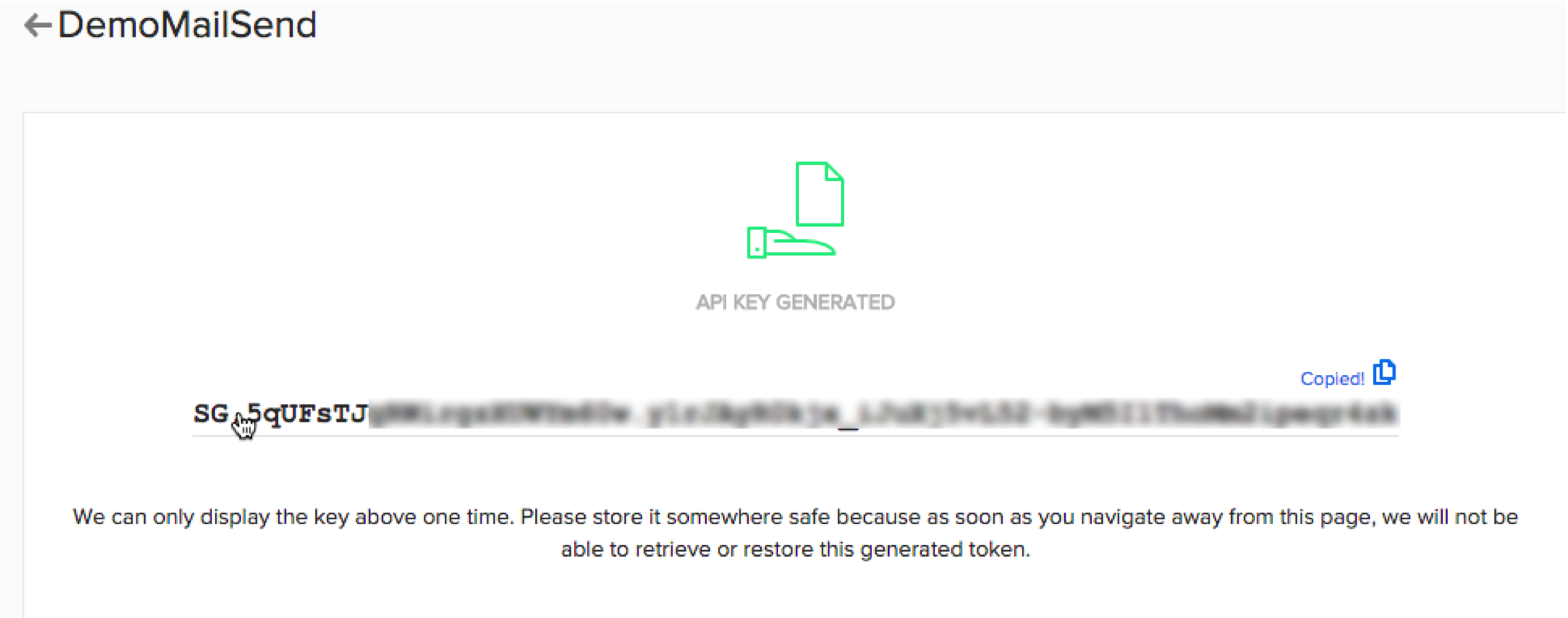
The key will be generated, and displayed on the screen only one time.
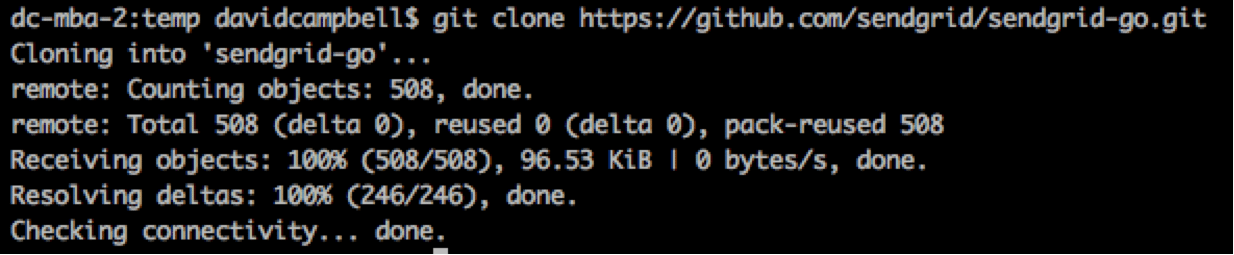
Now in a separate browser tab, navigate to the
SendGrid Go library. Clone it however you like. I prefer the terminal.
Now change to the SendGrid-Go directory (cd sendgrid-go) and copy the sendgrid.env.template to a file called sendgrid.env. (cp sendgrid.env.template sendgrid.env). sendgrid.env will be used to store your new API key on the filesystem.
However, we absolutely, positively don’t want this getting sent to GitHub, ever. So, use your favorite text editor to append .gitignore to include a line for “sendgrid.env”. This special file tells your git client NOT to send the file containing your API key to GitHub.

Now, we will again use your favorite text editor to write your API key into sendgrid.env.
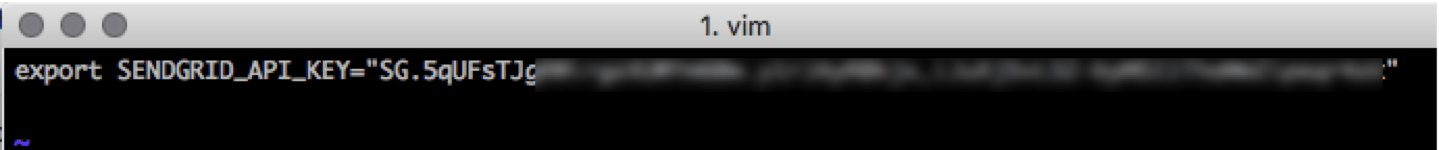
Save the file. Now source it (source sendgrid.env).
Copy and paste the Go example into a file (e.g. sendgrid-test.go).
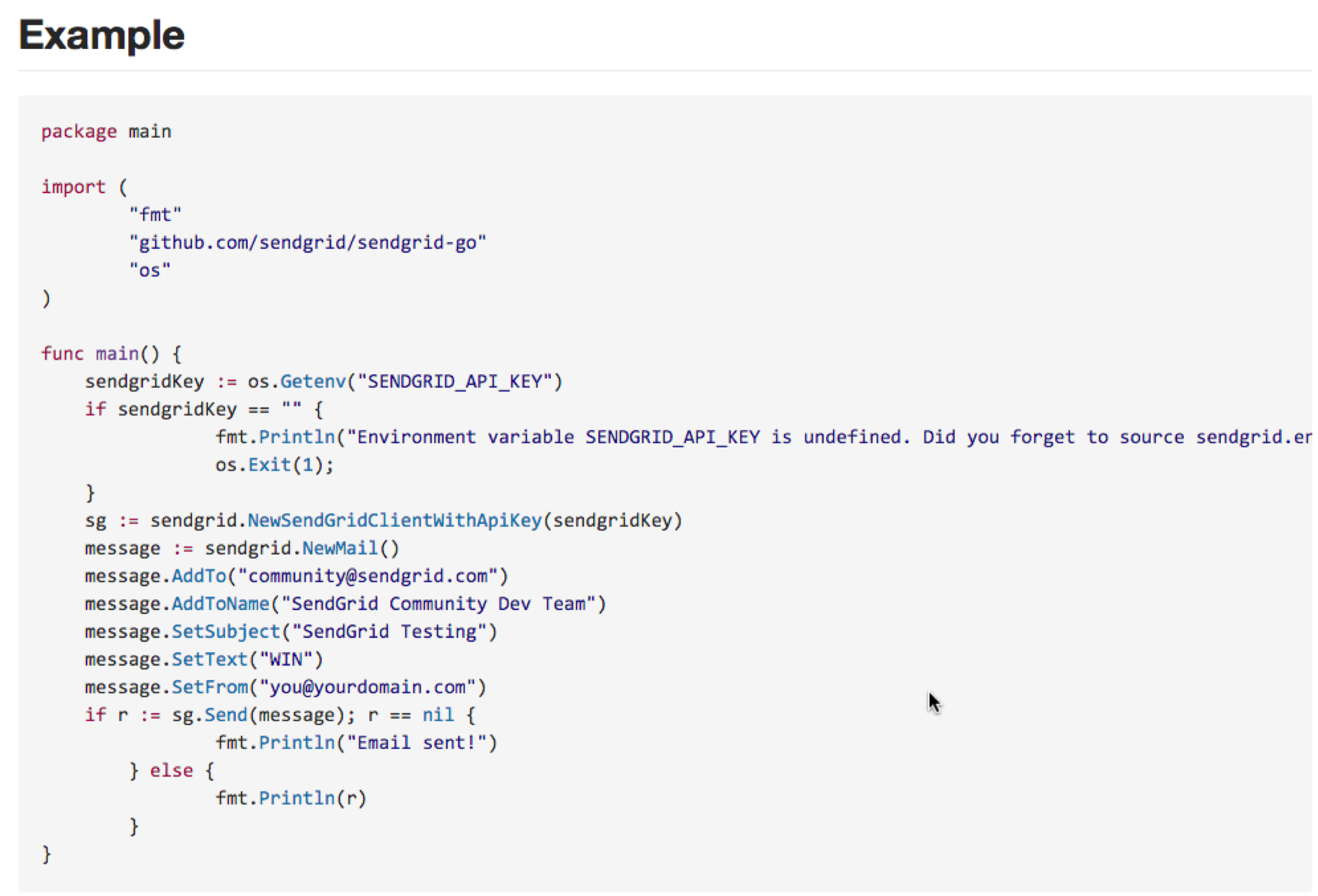
Now compile (go build sendgrid-test.go) and run (./sendgrid-test).
That’s it! With these simple steps you’re now using API keys instead of your SendGrid username and password to send your mail. Also, you’re safely calling your API key as an environment variable and storing it on the filesystem but never, ever sending it to GitHub.






