Send With Confidence
Partner with the email service trusted by developers and marketers for time-savings, scalability, and delivery expertise.

Time to read: 15 minutes
Tired of your legitimate emails landing in the spam folder? We can help.
Some emails deserve to go to spam—others don't. Learning how to stop emails from going to spam is an art and science, and we enjoy both aspects.
Email deliverability is not an exact science, which can be frustrating for senders of all types. You can accidentally end up in the email spam folder for several reasons, from your email list health to your authentication status. But there are a few tried-and-true tricks to help you land back in the inbox in no time.
Even the most seasoned email marketers experience email delivery issues—it happens all the time. That’s where we come in! We’re here to help you get back into the inbox and avoid the spam folder altogether.
In this post, we’ll cover some of our best advice to ensure your messages avoid spam filters and get delivered to your recipients. Look for tips regarding how to do the following:
Email content is vital for communicating important information to stakeholders, providing shipping confirmations or security alerts, etc., but it can’t help your recipients if the emails never make it to their inboxes or go to an unengaged audience. Always avoid:
You want an email list of folks interested in receiving your emails to ensure engagement. That's why organically building your email list is in your best interest long term. It may not be the easiest or fastest way to grow your list and audience, but it is by far the most effective.
For more on how to grow your email list organically and spammy email, check out our article, Grow Your Email List Like You Make New Friends.
Verifying recipient registration and opt-in is crucial to building a healthy, sustainable email list. Using a double opt-in ensures that subscribers consent to receive your emails by sending them a confirmation or welcome email that requires action, usually in the form of a check box or link agreeing to terms. Once they’ve completed this action, they are on your mailing list.
Here’s an example of a double opt-in in action from the Twilio SendGrid blog:
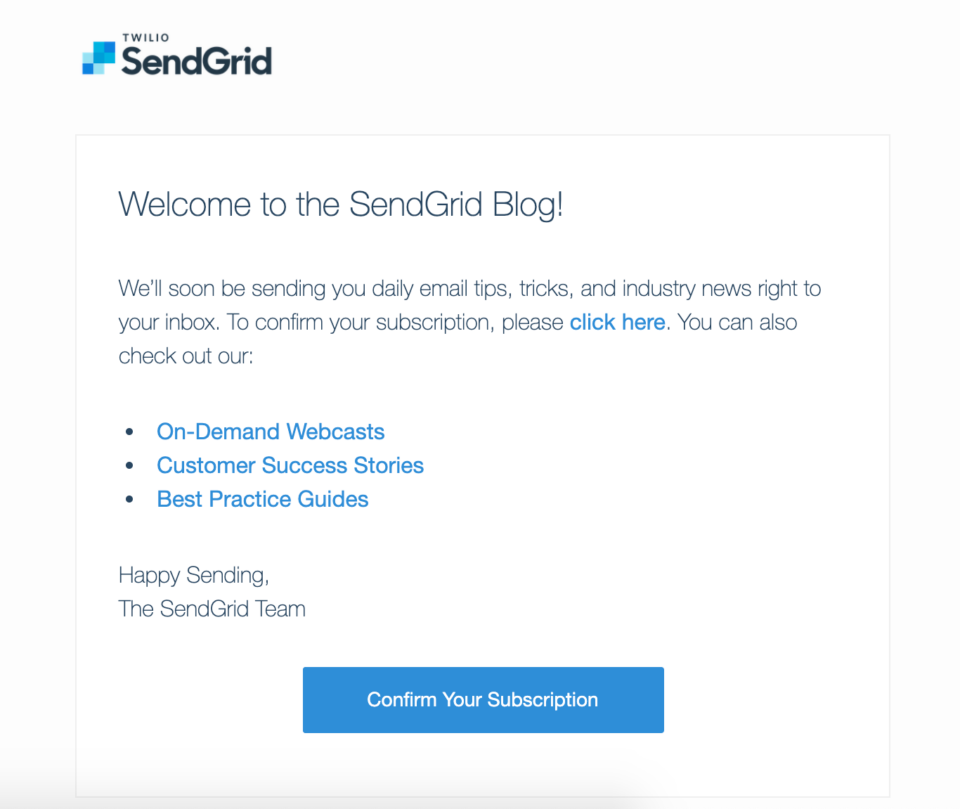
Utilizing double opt-in confirms a recipient’s genuine interest in your emails, keeping your engagement and delivery rates high while lowering your risk for spam traps. For more on best practices with sender-recipient relationships, check out our guide, Email Manners: A Tale of Two Senders.
Email authentication can be tricky but is key to verifying that you are who you say you are and that you’re sending legitimate emails. Inbox providers trust authenticated mail more than unauthenticated mail and are more likely to deliver those messages straight into the inbox.
The following 4 methods authenticate your email and help prove to providers that your email is worthy of the inbox and not the spam folder:
These authentication methods are the responsibility of the individual sender, but SendGrid can help you get started with each. Learn more about how our Expert Services can help you to mitigate deliverability issues and set your email program up for success.
Email lists and subscribers naturally ebb and flow as recipients drop off of your list. Some folks just don’t want to receive your emails, and that’s okay! The quality of your list is much more important and valuable than the number of contacts on your list.
While some individuals may unsubscribe, others will ignore your emails or mark them as spam. This is detrimental to your sending reputation, making your emails less likely to reach recipients' inboxes, including those that actively engage with your messages. A leaner, more engaged email list is always more effective than a large list of unengaged users.
Regular list maintenance helps stave off low engagement and its impact on your sender reputation. Removing unengaged users, bounced emails, and other spam traps are some of the most effective ways to clean your list.
Remember that email list turnover is normal—don’t take it personally! Be proactive, clean up your list, and you’ll experience improved delivery rates to the inbox.
Your email domain has an associated sending reputation, and if it begins to slip, you may find yourself on an email denylist. Even the most cautious and well-intentioned senders can end up on an email denylist occasionally. Reduce the risk of ending up on a denylist by implementing the following sending practices:
Keeping watch over your delivery rates will notify you of any signals that you may be on a denylist.
While compliance doesn't guarantee email delivery, it can help you bypass some internet service provider (ISP) roadblocks. Over the past 20 years, internet privacy laws have boomed around the world. The most important pieces of legislation for marketers and senders are Controlling the Assault of Non-Solicited Pornography and Marketing (CAN-SPAM), the Canada Anti-Spam Law (CASL), the General Data Protection Regulation (GDPR), and the California Consumer Protection Act (CCPA). These laws govern all commercial email, so let’s review what each asks of senders.
The Controlling the Assault of Non-Solicited Pornography and Marketing Act of 2003, or CAN-SPAM Act protects recipients' privacy by requiring senders to abide by a set of sending requirements and standards aiming to weed out bad actors.
Under CAN-SPAM, commercial communications must avoid deception by clearly stating the purpose of emails, respecting recipients’ preferences, and being transparent throughout the sending process. For more information on CAN-SPAM, check out 5 CAN-SPAM Myths & Best Practices: From a Lawyer’s POV.
The Canada Anti-Spam Law (CASL) serves a similar function to CAN-SPAM, aiming to create a more transparent relationship between senders and recipients. CASL applies specifically to commercial electronic messages (CEMs), defined as “any electronic message that encourages participation in a commercial activity, regardless of whether there is an expectation of profit.”
For an in-depth look at how CASL affects your sending practices, check out Canadian Anti-Spam Law: What You Need to Know.
Perhaps one of the most talked about pieces of privacy legislation in recent years, the General Data Protection Regulation (GDPR) has been top of mind for many since its inception in 2016. Its regulations cover the entirety of the EU, meaning that anyone sending email to the region must be compliant.
The GDPR aims to grant those in the EU more control over their personal data by requiring companies to be transparent with how they use it. Businesses working within the EU must be compliant with the regulation’s strict data processing requirements, covering where and how personal data is stored and used, as well as ensuring the security of that data.
For more information on the GDPR, read General Data Protection Regulation (GDPR): What Senders Need To Know.
The California Consumer Protection Act (CCPA) feels like the natural descendent of the above privacy legislation, granting consumers more control over the use of their data. However, it only applies to businesses falling within specific categories. For businesses to be subject to the CCPA’s requirements, only one of the following must apply:
Check out What Is the California Consumer Privacy Act? for more information on how the CCPA affects sending practices.
Remember, compliance with these pieces of legislation is obligatory, and meeting the requirements of one does not guarantee compliance with another. Err on the side of caution—you don't want to be an email spammer!
Preference centers provide new and existing subscribers with the freedom to adjust how often they receive your emails. By providing a preference center that puts recipients in control of how and when you contact them, you reduce the risk of having subscribers mark your emails as spam.
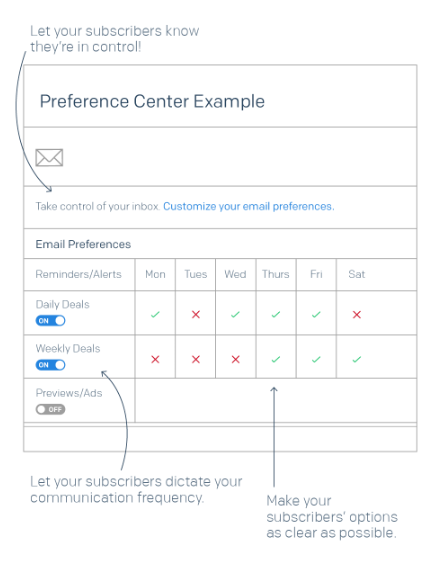
Reduce friction by making the preference center prominent and easy to access. Removing obstacles like this can actually help to increase your engagement rates and keep your messages in the inboxes of engaged recipients. Learn how to perfect your preference center.
Metrics and email performance are the tried-and-true way to know how your email program progresses and improves. Before you can utilize these key performance indicators, it’s important to understand your baseline metrics—we all have to start somewhere, right?
Start with the following basic metrics:
When you start tracking these metrics, don’t panic if you notice negative trends. The most important thing you can do is act quickly and calmly to remedy the problem. For example, in the case of dropping open rates, review your subject lines and email frequency. These 2 variables often have the most impact on this metric.
Also, when testing emails, use real content and recipients. Some practices, like seed testing, allow senders to test emails sent to small batches of recipients to understand how an ISP will respond but don’t provide a perfect analysis. Because every ISP weighs seed testing differently, try not to put all of your eggs in one basket here. In most cases, seed testing provides a false sense of security to senders—send tests to real recipients to get a more accurate idea of how they’ll respond.
The core of any successful email program is a commitment to sending relevant, interesting content to your recipients. This means being intentional about your sending practices and not sending for the sake of sending. Aimless sending can cause your engagement to suffer, and that’s the last thing we want. The emails you send should resonate with your recipients. Otherwise, you risk getting ignored—or worse, sent to spam.
The next time you draft an email, consider the following before hitting send:
Finding what email content works best for your brand often involves trial and error, so feel free to try new things and experiment with new styles of copy as you get to know your recipients.
Spam checkers are online tools that allow you to test your emails and indicate how likely recipients will mark them as spam. Although ISPs have the final say in how messages are filtered, spam checkers can often provide senders with peace of mind as they prepare new campaigns.
SendGrid’s email testing provides a spam-checking tool that shows how your emails may perform against some of the most powerful spam filters in the industry, as well as inbox rendering previews and URL checkers. Understanding how your emails may perform against these filters can help you to troubleshoot in advance and improve your likelihood of landing in the inbox the first time you send.
Crafting emails that resonate with each recipient isn't just about avoiding the spam folder—it's about building a connection. Segmenting your email list and personalizing the content lets you send emails that feel tailor-made for each subscriber. This boosts your engagement rates and decreases the likelihood of your recipients marking your messages as spam.
Begin by categorizing your subscribers based on relevant criteria such as their purchase history, geographical location, or engagement level. This segmentation allows you to tailor your messaging to fit the specific interests and needs of different groups. For instance, send a special offer to those who haven't purchased in a while, or a personalized product recommendation to frequent buyers.
Personalization goes beyond just inserting a subscriber’s name in the email. It’s about crafting content that speaks directly to their interests. Use data-driven insights to customize your emails with content that matters to each segment. Whether it’s a product update that's relevant to their usage or a helpful tip that aligns with their business goals, personalized touches can make your emails too good to ignore—and too relevant to be marked as spam.
Consistently reaching your subscribers' inboxes can sometimes be as simple as teaching them how to allowlist your email address. Taking this proactive approach safeguards your emails from inadvertently landing in the spam folder, helping to maintain your engagement rates and deliverability.
Start by including a brief, clear set of instructions on how to allowlist your emails in your welcome or confirmation emails. This guide should be easy to follow, catering to users who might not be as tech-savvy. Explain that by adding your email address to their contacts or safe senders list, they’ll ensure they never miss out on valuable information.
For example, you might include a simple step-by-step guide like this in your welcome email:
You can also provide links to detailed instructions for popular email services like Gmail, Outlook, and Yahoo to guarantee every subscriber knows exactly how to keep your emails front and center.
Your brand has been diligently collecting email addresses to ensure that each and every address you send to has opted in. You send your marketing messages at a consistent cadence. Your emails are compliant with CAN-SPAM and CASL, and you make sure to remove those folks who opt out or bounce.
And yet, you’ve heard from some subscribers that your messages are going to the spam folder. Even worse, you are noticing your overall open rates beginning to decline. But you aren’t a spammer! So, what gives?
It is highly likely your email is falling into the category we in the industry refer to as graymail. Graymail is an email that is not exactly spam but is not exactly wanted by recipients, either. At least, it is not always wanted.
Graymail is almost always sent from a legitimate sender to folks who have opted in, but it tends to generate low levels of engagement from recipients.
It wasn’t so long ago that most inbox providers viewed email as either spam or not spam. If an email looked malicious or appeared to be completely unsolicited, it would be filtered to the spam folder. If an email appeared to be something that recipients opted into, it would be delivered to the inbox.
As the volume of emails the average person receives continues to grow, inbox providers have found it necessary to stop viewing the world of spam as one that is black and white and widen their definition of what is and what is not spam. While their efforts do mean that more “legitimate” email is being filtered to the spam folder, the goal of these inbox providers is not to penalize marketers. Rather, their goal is to make sure that only wanted email makes the inbox so that their customers will continue using their product. This is an important point to keep in mind.
So, how do inbox providers determine what email is wanted and what email is not? Put simply, it’s all about engagement.
These are all things inbox providers such as Gmail and Yahoo are looking at to determine how engaged your recipients are with your messages.
The more positive engagement signals they see for your mailings, the more certain they will be that your email is wanted and the better your inbox placement will be.
Conversely, negative engagement signals such as spam complaints or large amounts of emails going unopened are all factors that contribute to more of your messages being filtered to the spam folder.
In the IT world, honeypots have a number of definitions depending on its usage, but with email, a honeypot means one thing—a trap. Honeypots are inactive email addresses set up specifically as a tool to catch spammers red-handed as these emails are not used by real people and, therefore, never opted-in to any email campaigns.
As a result, any mailer that sends to these addresses can be dubbed a spammer.
One of the most common ways that spammers obtain honeypot email addresses is by harvesting emails. They do this by:
Even legitimate mailers can end up with honeypots on their email file. Regardless of your intent, sending unwanted emails is a violation of the CAN-SPAM Act. That’s why it’s important for you to:
Not doing so can result in your IP being blocked or deny listed, which will compromise your email deliverability and response rates.
Email marketing provides a unique challenge in that every audience is different and prefers different types of content. The more you understand your audience and their email preferences, the better.
The strategies above can help you meet your audience where they are and give you a place to start. The rest is up to you. The higher your email engagement, the more likely you are to avoid email spam filters and land in the inbox—but it’s up to you to stay there.
Email is constantly evolving, which means best practices are too. Stay up to date by checking out our annually updated Email Deliverability Guide. Our Expert Services are also here to help you through specific obstacles within your email program. Wondering how to keep your emails from going to spam? Here are our top tips to keep your emails out of the spam folder and into the inbox.
Partner with the email service trusted by developers and marketers for time-savings, scalability, and delivery expertise.